- Email: office@safebyte.io
- Bucharest, ROU

Using a combination of manual and dynamic analysis and testing along with custom automated fuzzing, SafeByte’s Mobile Security Testing covers areas such as:
For open mobile platforms such as Android, mobile applications are also decompiled to maximize understanding and testing coverage. For closed platforms such as iOS, source code is often requested to accompany the engagement or binaries can be reversed at runtime.
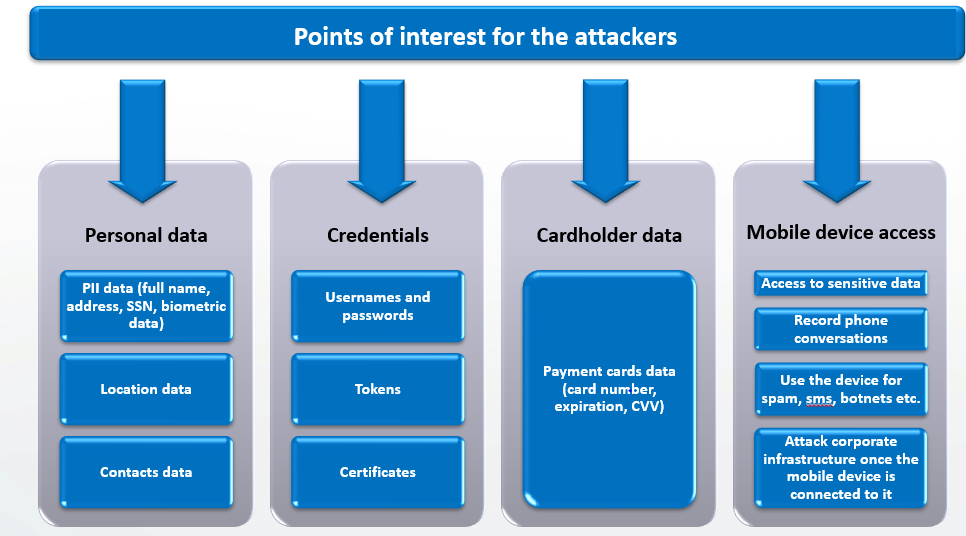
Our engineers begin the assessment by evaluating data protection controls on the client device. In particular, the engineers will examine where and how the application manages sensitive information, whether the application is properly utilizing native APIs for features like key stores, and whether dangerous client artefacts such as user credentials, personal information or any other sensitive application data is unintentionally or insecurely stored on the phone.
Application package analysis – unpack the application bundles for the Android and iOS operating systems. An analysis should be done to assure that there are no changes in configurations of the compiled binary and no sensitive data is left in the packet like private keys, logs and so on.
Reverse engineering – For open mobile platforms such as Android, mobile applications are also decompiled to maximize understanding and testing coverage. For closed platforms such as iOS, source code is often requested to accompany the engagement or binaries can be reversed at runtime.
Static analysis – The application is not executed, the investigation is performed on the obtained files from previous step.
Dynamic analysis – we review the mobile application’s behaviour on the device or emulator. Tests performed here include a forensic examination of the file system, assessment of the network communication between the application and server (SSL Pinning), evaluation of the application’s inter-process communication (IPC), root/jailbreak detection and other specific tests.
File system analysis – we examine the local files written on the file system by the application to assure that the application does not have insecure permissions, cannot access files outside it’s container and does not leave sensitive files unprotected at rest.
Inter-Process Communication Endpoint Analysis – we review the different mobile application IPC endpoints:
Content providers – these ensure that access to databases is controlled.
Intents – these are signals used to send messages between components of the android system.
Broadcast receivers – these receive and act on intents received from other applications on the android system.
Activities – these build up the screens or pages within the application.
Services – These run from the background and perform tasks regardless of whether the main application is running.
Using commercial, open source, and proprietary tools, SafeByte implements a structured testing methodology based on OWASP’s Mobile Security Testing Guide (MSTG) to make the mobile application assessment as efficient as possible. During the testing, we simulate a multitude of attacks, both general application attacks and mobile dedicated attacks. The testing simulates a real hacker and what he can do to penetrate the application and retrieve confidential information.
Mobile penetration testing will present the real-world attack vectors that could impact an organization’s assets – data, humans or physical security. A pentest should ultimately reveal you how effective your security controls are against these attacks.
Wi-Fi is a preferred way for attackers to infiltrate into an organization’s internal network and
Read MoreWe have specialized in providing best Penetration Testing services, adapted to your needs.
Read MoreIdentify vulnerabilities in your web applications using manual testing process customized for your project.
Read More